Deux nouveaux custom plugins sont disponibles sur le github de Security Copilot Defender Device Investigation et Defender Device Info.
Il faut tout d’abord les installer et pour ce faire récupérer les fichiers YAML sur github :
Puis le bouton au nouveau du prompt :

Je reste sur Plugins et je descend jusqu’à Custom :
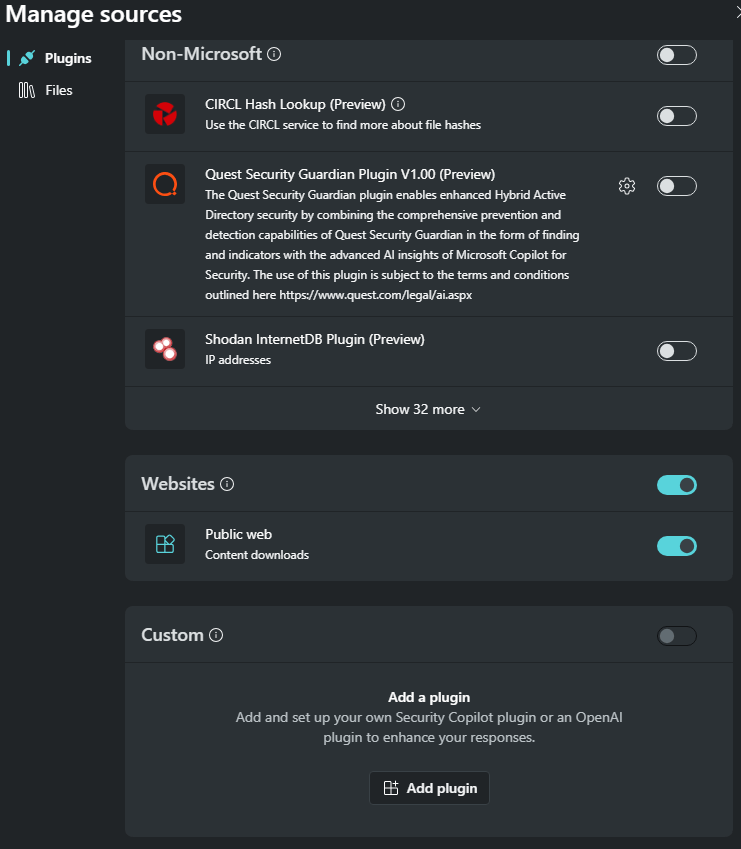
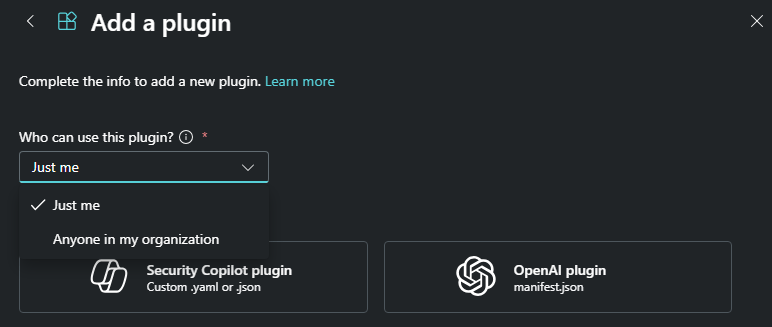
Add plugin, pour moi ou pour tout le monde
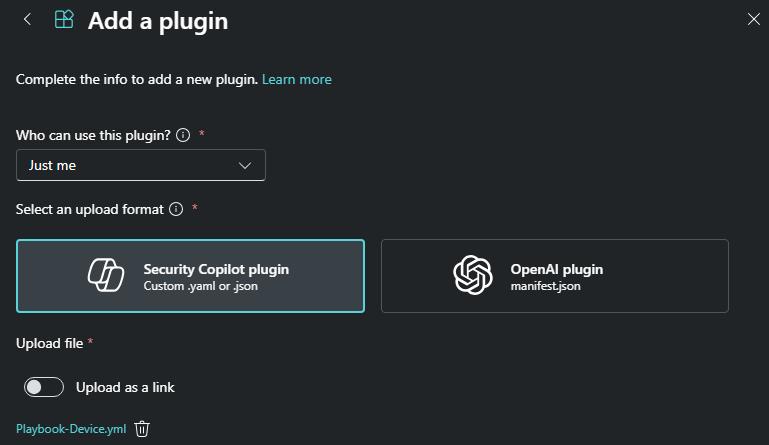
J’ajoute les plugins un par un
et je les retrouve désormais dans ma liste de plugins
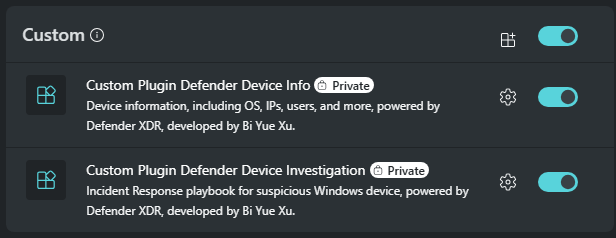
Je n’ai maintenant plus qu’à les utiliser dans le prompt via System capabilities et mes custom plugins :
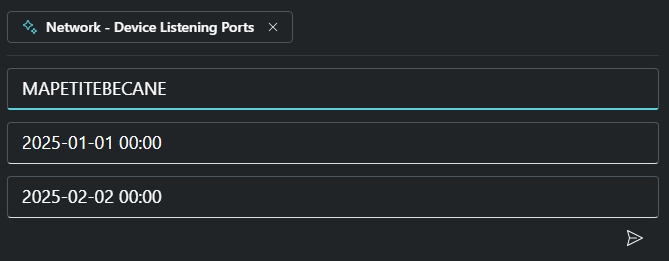
Il faudra bien sûr ensuite entrer des paramètres comme ici le nom du périphérique et la période :
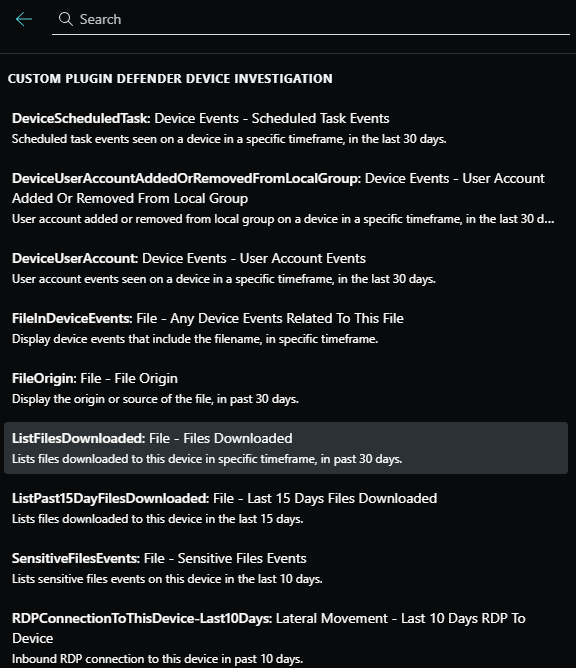
Et le tour est joué ! On peut récupérer les activités suivantes :
Title: File – Files Downloaded
- Description: Lists files downloaded to this device in specific timeframe within past 30 days.
Title: File – Last 15 Days Files Downloaded
- Description: Lists files downloaded to this device in the last 15 days.
Title: File – Any Device Events Related To This File
- Description: Display device events that include the filename, in specific timeframe.
Title: File – Sensitive Files Events
- Description: Lists sensitive files events on this device in the last 10 days.
Title: File – File Origin
- Description: Display the origin or source of the file, in past 30 days.
Title: Process – Process Executions Summary
- Description: Summary of process executions on this device in specific timeframe.
Title: Process – Detailed Process Executions
- Description: Detailed all process execution events on device within a brief period, e.g. an hour.
Title: Process – Detailed Process Events
- Description: Detailed specific process execution events on device within a defined time frame.
Title: Lateral Movement – RDP To Device
- Description: Inbound RDP connection to this device in a specific timeframe.
Title: Lateral Movement – Logon To Device
- Description: Logon events from other devices to this device in a specific timeframe.
Title: Lateral Movement – Logons To Device In Last 10 Days
- Description: Logon events from other devices to this device in the last 10 days.
Title: Network – Outbound Network Events
- Description: Device outbound network events, including attempts and failed connections.
Title: Network – Inbound Network Events
- Description: Device inbound network events and attempts in a specific timeframe.
Title: Network – Device Listening Ports
- Description: Displays device listening ports in specific timeframe.
Title: Device Events – Scheduled Task Events
- Description: Scheduled task events seen on a device in a specific timeframe.
Title: Device Events – User Account Events
- Description: User account events seen on a device in a specific timeframe.
Title: Device Events – User Account Added Or Removed From Local Group
- Description: User account added or removed from local group in a specific timeframe.
Title: Suspicious Activities – ASR Rules Triggered
- Description: ASR rules that were triggered on this device in the past 7 days.
Title: Suspicious Activities – ASMSI Script Detection
- Description: Script detection from Windows Antimalware Scan Interface (AMSI) in past 7 days.
Title: Suspicious Activities – Exploit Guard Events
- Description: Exploit Guard events detected on this device in past 7 days.
Title: Suspicious Activities – Network Protection Events
- Description: Network Protection events triggered on this device in the past 7 days.
Title: Suspicious Activities – Device Tampering Attempts
- Description: Possible tampering attempts on this device in the past 7 days.
The second custom plugin, “Custom Plugin Defender Device Info”, offers specific device information often needed during an investigation. Its skills include:
Title: Device OS Information
- Description: Latest device OS information with the device name as the input.
Title: Device Current and Past IPs
- Description: The current and past IPs assigned to this device in the last 10 days.
Title: Device Users and Login Counts
- Description: List users logged onto this device and the number of times, within the last 10 days.
Title: Device Alert Information
- Description: Alerts observed on this device in the last 30 days.
Title: Device Installed Applications
- Description: Currently installed applications on this device.
Title: Device Vulnerability Information
- Description: Vulnerabilities identified on this device.
Title: Device Critical Vulnerabilities
Description: Vulnerability with CVSS score 7 or higher, or exploit is publicly available.
Plus d’informations dans le blog Next-Gen Device Incident Investigation & Threat Hunting with Custom Plugins

Laisser un commentaire